The physical cyber threat has reached our plants.
For a long time, cybercrime has been interested in data theft and in stealing money. The entire ecosystem had integrated it into its costs and thus banks accrued for a gentle 2 to 3% contingency provision to deal with these repeated thefts.
Now cyberattacks move to industrial sites where they somehow threaten the lives of those who work there and those who live around. As a consequence, it changes the scale of risk borne by companies. Before when you worked on securing an e-commerce site, you were pretty much aware of the issues. Now it’s different because the loss of a human life cannot be accrued for with a provision of a few percents of the company’s turnover.
An amazing speech was delivered at the 2018 SXSW by a young consultant and hacking expert Mark Nunnikhoven. He presented an alarming study by Verizon highlighting that most plants worldwide are vulnerable and poorly protected as they were built on a completely outdated architecture which cannot be updated remotely. There is little choice other than having to work with it for another 10 -15 years, the average amortization period of these plants.
His demonstration is simply reminding us that factories are built for 30 years, robots for 15 years whereas new attacks and new threats come every second. As we will not close these plants simply because of a threat, we have to find ways to limit the consequences of their vulnerability.
The origin:
Phishing techniques to sneak into an information system and then to be able to remotely control it without changing the point parameters was developed by the CIA and was released in 2010 after they had managed to remotely disable all of the gas centrifuge enrichment plants. In 2015, a German blast furnace was damaged by a remote phishing attack.
Now all hackers in the world master these techniques and, according to the report from Verizon, the success rate of phishing attacks targeting industry reached 13% in 2017. Israeli experts that we met in January 2018 in Tel Aviv voiced their concern and admitted that the hackers have the advantage for the time being: 50% of « industrial accidents » would be of industrial cybercriminal origin..
Technically, the cyberthreat to the industry is the consequence of a stack of causes: no encryption, old softwares, no authentication, insecure interfaces, no « code signing », unmodified standard PassWords, not possibility to install security patches remotely ..
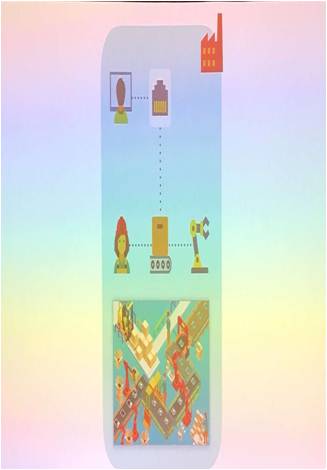
 How did we get there? Simply because we started from existing old manufacturing infrastructures including locally controlled robots. Then we attempted to control them remotely, first from control rooms via Scada (see photo aside). Lately, in the age of big data era, we connected all robots of all factories together to upload data to the corporate level, thereby increasing the risk of intrusion. (see diagram below)
How did we get there? Simply because we started from existing old manufacturing infrastructures including locally controlled robots. Then we attempted to control them remotely, first from control rooms via Scada (see photo aside). Lately, in the age of big data era, we connected all robots of all factories together to upload data to the corporate level, thereby increasing the risk of intrusion. (see diagram below)
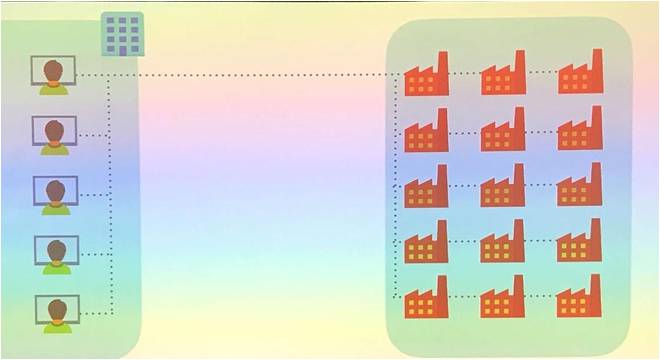
NOW: ⇒ all logged together inducing more vulnerabilities
BEFORE: Local
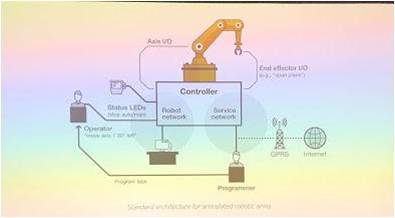
Each robot is typically connected to two networks: a local network processor and a service network. This leads to a dual vulnerability to phishing attacks.
Threats and attacks
Today, industrial sites are the 2nd target of hackers after health sites. The plants represent 17% of GNP and hackers quickly realized what potential they represent. In order to extort money from your company , they have a choice of options:
- take remote control of one or several robot(s)
- change the alarms
- change the settings of some text files that will dictate the robot to work differently.
Example: In a video Mark Nunnikhoven showed us how the malware would just change the robot configuration in a text file without changing the code of the robot. As a consequence it would alter imperceptibly its way of working in its environment. The airplane wing under manufacturing would then come out with flaws of maybe a few tenths of a millimeter, rendering it dangerous and unusable … without anyone noticing at your level of certified tier one subcontractor…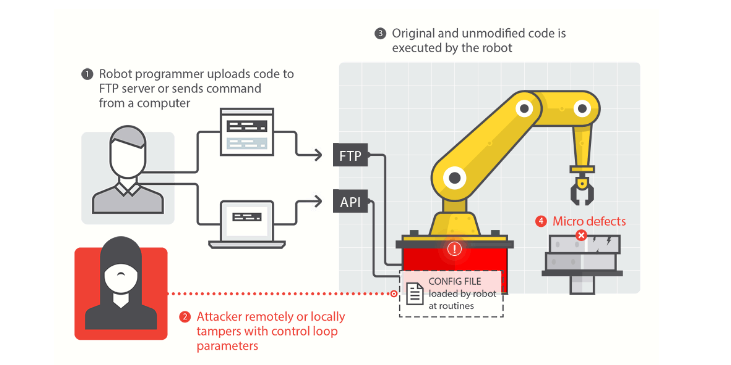
What should you do?
No. 1 priority of all plants is always employee safety and security with lots of regulations , stacking labor law and social law (Hygiene and Security Committee, Safety Commission , etc…) None places cyber defence high on the priority list although robots could potentially harm employees is they are remotely spoofed to become destructive weapons against operators. It is urgent to put this issue at the center of plant safety.
And above all , fully assess your industrial cyber security vulnerability and level of internal expertise with an external expert body or individual before moving into manufacturing 4.0 or industry 4.0 with IoT everywhere.
For more info, see the items for our collective curation on Flipboard Internet InnoCherche

